What is IT Infrastructure?
Performance Optimization Through Proven Settings
B2B I.T. Solutions applies proprietary optimization settings refined over 25 years to improve computer system speed and responsiveness. These settings are designed to streamline how each computer operates, reducing delays and improving the overall user experience. Technicians apply proven adjustments that help systems respond faster to commands, load applications more efficiently, and maintain consistent performance throughout the workday. This process is part of our broader IT service management strategy, which focuses on reliable and responsive technology support. Depending on the age of the computer systems, most businesses benefit from smoother computer operations without the need to invest in new hardware or complex upgrades.

To improve system responsiveness, B2B I.T. Solutions reviews and uses a custom designed multi-point inspection that checks many things, a few of which reduce non-necessary junk files, optimizes computer settings and reduces background activity that slows down computers during regular use. By limiting non-essential processes, technicians help ensure that business tools open quickly and operate with minimal to no delay from the operating system. Our method supports smoother navigation and faster access to commonly used programs, even on older systems. The adjustments are applied consistently across all supported devices, creating a more efficient work environment. These performance improvements are maintained through ongoing IT service management, allowing businesses to stay productive without interference from the technicians.
In our commitment to maintaining peak performance across all computers, B2B I.T. Solutions applies a proven configuration that supports business-critical software applications. Each computer system is reviewed regularly to ensure that the performance settings remain intact and continue to deliver consistent results. This proactive approach to IT service management helps prevent slowdowns before they occur, keeping workstations responsive and reliable.
The optimization process is included as part of standard support for all clients receiving ongoing IT service management. Technicians incorporate these performance checks into scheduled service routines, ensuring that each system continues to meet operational standards. This coverage applies uniformly across all managed devices, with no additional action required from the client.
Recurring Maintenance for System Reliability
Recurring computer maintenance is a core part of how B2B I.T. Solutions delivers proactive system care. Technicians follow a proprietary checklist during scheduled service intervals to remove unnecessary files, verify system integrity, and confirm that performance settings remain in place. These tasks are designed to prevent slowdowns and maintain optimal speed across all supported devices. As part of ongoing IT service management, this maintenance routine helps ensure that systems stay clean and fast. Our custom designed process allows technicians to maintain the computer at peak performance without interrupting business operations.

Software updates, critical patches, system checks and more are completed through a central server system that avoids interfering with employee tasks. B2B I.T. Solutions schedules these actions during designated maintenance windows to prevent slowdowns or interruptions. Technicians follow a consistent IT service management routine that ensures updates are applied efficiently and system checks are completed with minimal to no involvement required from the employee.
Recurring maintenance plays a critical role in preventing gradual performance degradation across computer systems. Over time, computers can accumulate outdated files, misaligned settings, and minor software issues that significantly reduce speed and stability. B2B I.T. Solutions addresses these concerns through scheduled maintenance service that restores optimal performance before minor issues build up and escalate into major problems. All of this is part of our ongoing IT service management. Regular attention to computer system health helps ensure that devices continue to perform consistently without requiring frequent repairs or emergency interventions.
The care provided to the computers is delivered uniformly across all devices covered under contract, ensuring that each system receives the same level of care and attention. B2B I.T. Solutions applies a standardized process that allows technicians to perform inspections and updates with consistency, regardless of device age or usage. Our approach to IT service management ensures that every workstation remains aligned with the company’s performance standards.
Integrated Cybersecurity Protection
B2B I.T. Solutions includes zero trust cybersecurity tools as part of every IT service management support contract to block digital threats. The safeguards are designed to prevent any unauthorized program from launching on the computer, stop malicious websites from loading, and reduce exposure to hidden risks that can quietly disrupt business operations. Rather than relying on basic protections alone, our coverage combines a multi-layer solution that works together to detect and prevent harmful activity. This approach ensures that every workstation receives consistent protection, with safeguards tailored to the business environment. Our process reflects the principles of IT service management, where security is built into daily business operations.

Cybersecurity protections are actively managed by our highly trained cyberhero division who monitors threat activity, apply updates, and verifies that each safeguard remains properly configured. This oversight ensures that protections are not only installed but maintained with precision. Technicians follow a documented checklist that includes configuration review, and validation of system behavior. This disciplined approach prevents setup errors and ensures that protections are not only installed but actively maintained.
Security protections function quietly in the background, keeping systems secure without interfering with performance. These safeguards are active at all times, monitoring behavior and preventing unauthorized actions while allowing teams to complete their work with minimal to no disruption. Our silent operation helps maintain productivity across business environments, ensuring that protection does not get in the way of daily responsibilities. B2B I.T. Solutions applies this method consistently, delivering zero trust cybersecurity that supports business operations without drawing attention away from business production. This approach and more are at the of our principles for IT service management, where security is present but never obstructive.
Strict software application control is enforced through a zero trust model that treats all software as unapproved until explicitly authorized. This approach blocks unknown programs from launching, even if they attempt to run through system features or computer trusted software. Each application is reviewed before gaining access to the critical computer system tools, reducing exposure to ransomware, fileless malware, and significantly reducing the computers exposure to hackers and scammers. Through its IT service management contracts, B2B I.T. Solutions applies this level of control at the operating system level, ensuring that only verified software can run on that computer.
Scalable Support with Direct Technician Access
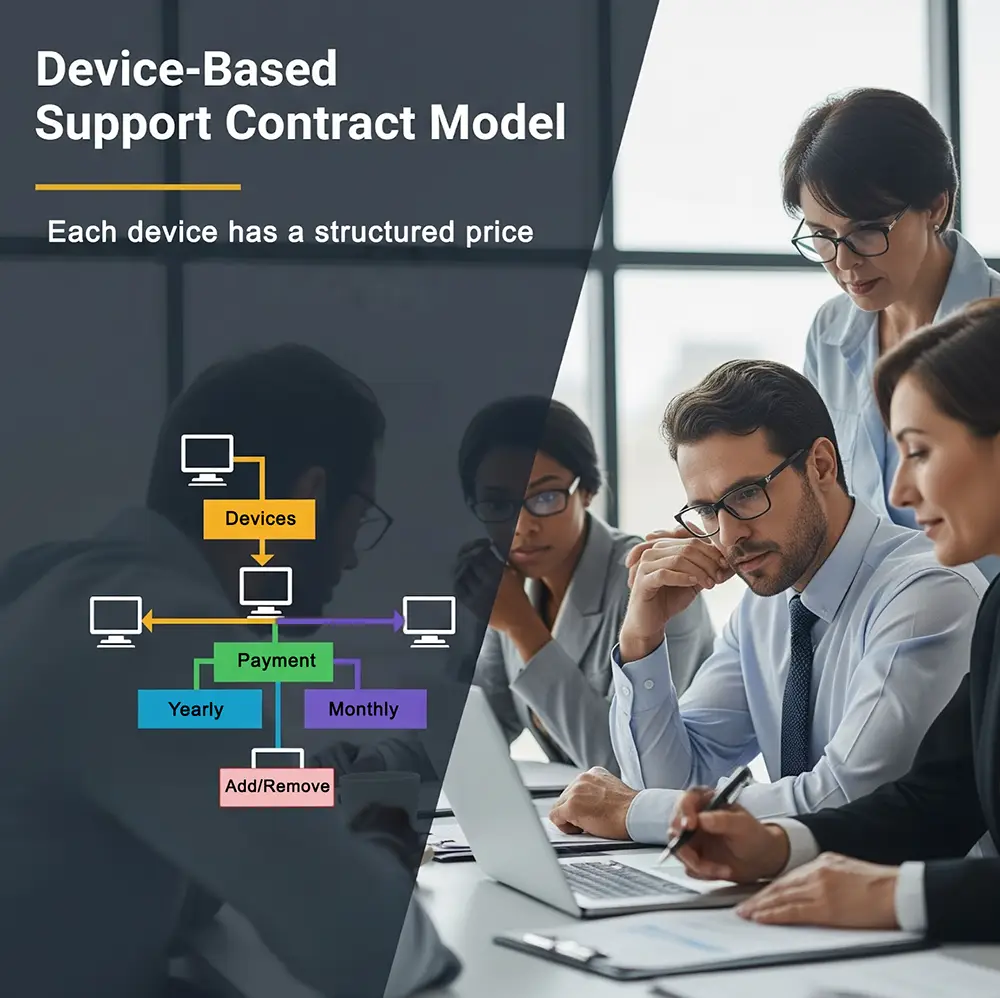
Support contracts are structured around the number of computers being maintained, not the number of employees using them. This model allows businesses to scale their service needs based on actual device count, making budgeting more predictable and straightforward. B2B I.T. Solutions focuses on the systems that require care, ensuring that each workstation receives full support regardless of how many users access it. This approach eliminates confusion around user-based billing and keeps service delivery aligned with real infrastructure requirements. As part of our IT service management strategy, this structure ensures fairness, clarity, and consistent coverage across all supported devices.
Each client may designate a primary point of contact who is authorized to submit support requests directly to our technicians. This streamlined communication channel ensures that service requests are submitted accurately and resolved efficiently, without delays caused by third-party intermediaries or generalized help desk queues. The designated contact works directly with our team, allowing for faster troubleshooting, clearer issue reporting, and more responsive service delivery. As part of our IT service management framework, this direct-access model ensures that technical support is expedient and remains in alignment with our clients business priorities.